With cyber-attacks on businesses on the rise, manufacturing facilities are now increasingly at risk. We take a look at the security vulnerabilities that allow these intrusions to take place and what you can do to prevent cyber-attacks from targeting your manufacturing facility.
Just how bad is cyber-crime these days? The answer is pretty bad. You can’t hardly look at the news without learning about yet another major business that’s been attacked. For example, in just the past week, DNA testing service MyHeritage reported that 92 million of their customer email addresses were exposed.
This comes on the heels of a series of recent attacks on restaurant chains. Did you eat at any of one of Chili’s 1,600 restaurant locations? Malware may have compromised your credit card. Same story if you recently ate at an Applebee’s restaurant. Meanwhile, over at Panera Bread, customer data may have been exposed on their company website for months.
The stakes for companies that suffer breaches are high. The retail industry got a major wakeup call in 2013 when it was discovered that hackers had obtained the names and credit card numbers of 70 million Target store customers, which they subsequently sold on the black market. Target had to pay out over $18 million to settle the lawsuits filed by 47 state attorneys general. But that was just a down-payment. Target reportedly spent more than 10 times that amount ($200 million dollars) to resolve the issue.
Today, the situation facing a company like Target could be worse, especially if they were based in the EU, or had customers in Europe.
The European Union’s new General Data Protection Regulation (GDPR) law (which went into effect on May 25, 2018) enables regulators to fine European businesses — or those with European clients — who fail to protect private consumer data a minimum fine of €20 million euros (approx. $23.5 million dollars) rising to as much as 4% of a company’s annual worldwide turnover from the preceding fiscal year.
To put this fine in perspective, Target’s 2017 revenue was $71.879 billion. Had they been a European company subject to the maximum GDPR fine, they could have been required to pay out an eye-watering $2,875,160,000 restitution fine for their security breach — an amount that’s over 10 times more than what the company spent to resolve their 2013 breach in the USA!
Cyber-Attacks on Businesses May Expand to Manufacturing Facilities with Weak ICS Cyber-Security Protection
So far, we’ve only mentioned what’s been happening to customer-facing retail businesses. But, as cyber-attacks on businesses increase, manufacturing companies need to take heed — because they may find themselves in the cross-hairs as cyber-criminals widen their sights on vulnerable businesses.
This is not good news for manufacturing companies, which may be inherently more vulnerable to cyber-espionage and cyber-attacks than other industries, such as retail.
Why are manufacturers potentially at greater risk? Compared to retail companies, whose risk is primarily related to inventory control and customer payment systems, manufacturers have to manage all the elements under the umbrella of Industrial Control Systems (ICS) cyber-security. This includes Supervisory Control and Data Acquisition (SCADA) security, distributed control system (DCS) security, and protecting programmable logic controllers (PLCs).
In plain English, this means manufacturers have to secure a wide variety of process control systems, instrumentation and safety monitoring systems, and vendor supply chain systems — all of which are potential targets for cyber-criminals.
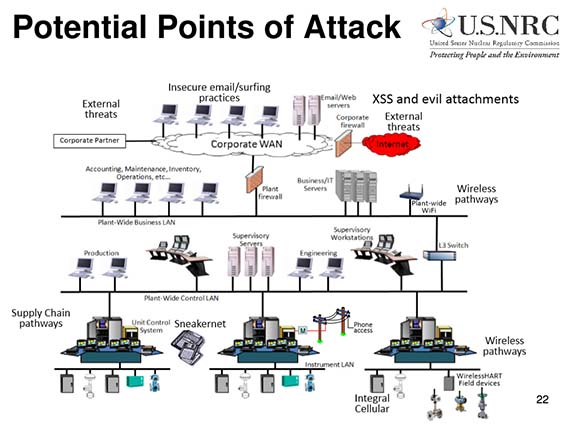
Further compounding the problem are the security vulnerabilities arising from legacy or orphaned hardware and software systems commonly used in manufacturing processes — many of which were built before Internet security was a consideration. Software patches and hardware upgrades can be hard to come by as well, especially if the original vendors have gone out of business or are no longer providing software patches or a viable hardware upgrade path.
To top it off, there are quite a few plants in the heavy industry manufacturing category (including chemical processing, paper and pulp production, energy generation, and oil and gas refining) that have production line processes that are designed to run continuously for years at a time, sometimes for the lifetime of the plant. This makes it very difficult to shutdown the plant to perform hardware upgrades or software patches — if they are even available.
To learn more, let’s take a look at three different cyber-attack scenarios currently affecting the manufacturing sector.
1. Industrial Espionage
Industrial espionage may be the most “traditional” form of attack on manufacturers. Trade secrets, design blueprints, production plans, pricing lists for raw materials are all examples of confidential materials that, if they were to fall into the hands of an unscrupulous competitor (or foreign government), could give them an unfair competitive advantage.
While stealing information in the past required spying techniques, such as making microfilm copies of documents, today’s cyber-criminals can break into corporate networks and surreptitiously copy electronic data.
Accessing and copying files may also be less “obvious” than other types of intrusions (such as stealing credit card data), so manufacturers need to be alert to unauthorized access and evidence of “touched” files. Unfortunately, complicit insiders can be a risk factor to this type of cyber-crime; rather than hacking into a network, a bad employee with a thumb drive may be all that’s needed to steal massive amounts of sensitive data.
These industrial espionage cases are rarely reported. An exception is the German steel conglomerate ThyssenKrupp. In 2016, it was hit by a cyber-espionage attack conducted by hackers based in Southeast Asia that affected its Industrial Solutions and Steel Europe business divisions. Details, however, remain vague on what was actually stolen and the impact on the company.
Ringfencing critical data into smaller, isolated networks that are accessed on a “need-to-know” basis can help defend against losses due to industrial espionage.
2. Financial Crimes, Including Ransomware
Most cyber-attacks on businesses, such as giant retail chains or healthcare institutions are motivated by financial gain. Selling millions credit card numbers on the black market is lucrative. So too is stealing and selling personal data (especially healthcare records, which are quite detailed) which can be used to create fake identities that can be used for claiming fraudulent tax return refunds or opening up new credit accounts.
As a result, those manufacturers without a large direct customer base were typically ignored by cyber-criminals looking for financial crime targets.
Unfortunately, that’s changing. For example, cyber-criminals were able to enter the accounting system of a Boeing aerospace vendor, Austria-based FACC Operations GmbH. Once they had access to the banking information, the hackers were reportedly able to transfer corporate funds out of the company’s bank account. FACC reports damages totaling $55 million dollars.
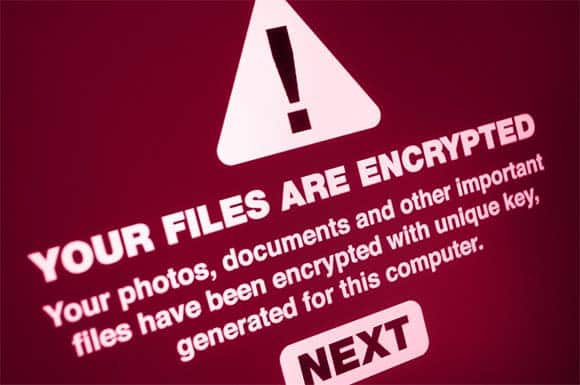
More recently a new form of cyber-attack has emerged: Ransomware. As the name implies, the attackers hold something hostage: in this case, it’s your data. Once they’ve gained control over your computer network, hackers are able to access your data and encrypt it with a secret key — rendering all corporate data systems helpless unless a huge ransom is paid. While most media covered the ransomware attacks on the British National Health System (NHS), a similar extortion threat was made against a North Carolina-based transmission parts supplier, AW North Carolina, that builds components for Toyota.
3. Attacks on Facilities and Infrastructure
Our third example is even more troubling. While it’s easy to understand the motivation of criminals stealing valuable industrial information, or of hackers diverting funds from a company’s bank account, there is an emerging threat to manufacturing facilities and supporting infrastructure where the goal simply seems to be the destruction of production equipment.
For example, clues in a German security briefing point to an unusual case where an unnamed German steel mill lost control of one of their blast furnaces. Without any ability to control the furnace, e.g. shutting it down, it was at risk of overheating and fire. This attack was carried out by first breaking into the company’s business side using a phishing attack — more on that later — and then a step-by-step attack on the process control systems.
In Saudi Arabia, an un-named critical infrastructure plant was attacked by cyber-criminals and shut down entirely. It is thought that the attack was achieved by first gaining access to the industrial safety system, Triconex, from Swedish-based Schneider Electric SE. Triconex is widely used in oil and gas production facilities as well as nuclear power plants.
It is unknown (or perhaps more precisely, not public information) who conducted the attacks. It is thought they could be pre-cursors or test runs conducted prior to a full-scale cyber-war. By compromising the safety systems, plant operators would not be aware of the full scale of damage due to an attack until it was already well underway.
How to Prevent Cyber-Attacks at Your Industrial or Manufacturing Facility
To learn more about practical steps you can take to prevent cyber-attacks on business and industrial processes at your manufacturing facility, we spoke with Arlen Peckham, the President and Founder of Lithium Networks, which is the consulting firm managing IT infrastructure here at Formaspace.
Given his company’s long experience in managing IT systems for different manufacturing facilities, we wanted to know first-hand what advice Peckham could give us on how to make you and your company less vulnerable to cyber-attacks.
Based on Peckham’s input, we’ve created a list of the top nine tips for how to manage the people, processes, networks, hardware and software — and more — that will keep you one step ahead of cyber-criminals.
Nine Cyber-Attack Risk Sources and How to Manage Them
1. Personnel Risks
According to Peckham, people in your organization are the greatest risk for cyber-security. The vast majority of employees want to do the right thing, but they need training on good security hygiene. It’s important that they learn how to use 2-factor security (using either a code sent to their mobile phone or an authenticator app, such as Google Authenticator) to prevent unauthorized access into any account they have. Using a password vault, such as the free Password Safe, can help end users create sufficiently complex passwords. Teach employees to never re-use the same password for different accounts. Also, educate them on the importance of verifying emails that may be fake (an attack mode known as Phishing) by confirming with the purported sender that the email is valid before providing confidential data, entering usernames and passwords, or opening email attachments.
Create corporate policies about using portable storage, especially thumb drives, which may come already infected with malware. Finally, keep data segregated into smaller networks that can only be accessed on a need-to-know basis to reduce the amount of data a cyber-criminal has access to should they be able to break into a network.
2. Vendor Risks
Complex supply chains operate more efficiently when data is shared between you and your vendors. However, this also increases the risk of cyber-attacks on businesses if your network or your vendor’s network becomes compromised. Vet your business partners carefully and conduct regular security audits to make sure they are keeping any shared data safe. Make sure you have proper legal indemnifications in place in case they suffer a cyber-attack.
Physical access to computer equipment and network cables is another possible vector for cyber-attack. Bad actors posing as cleaning companies or maintenance teams could take advantage of behind the scenes access to change physical networks by adding additional gear to perform “man-in-the-middle” attacks that can intercept your electronic data communications.
Finally, choose hardware and software vendors that are both reputable and dependable. Your investment in IT and industrial control systems will be lost if your supplier cannot keep up with security patches and hardware upgrades that protect you from cyber-attacks on businesses.
3. Remote Access Risks
When working outside the office, make sure your laptop or tablet or phone is secure and locked. Don’t keep sensitive information on these devices. If you leave a briefcase in the taxi or on a train, you don’t want your company’s contracts, customer lists, or other sensitive data at risk. The open wireless connection at the local coffee shop is also a potential source of data theft due to “man-in-the-middle” attacks or other malware. Always use a secure virtual private network (VPN) to connect to the Internet, even when you are just reading online news.
Cell phone calls are another risk. Sensitive information can be overheard when you are speaking too loudly. There is also new evidence that some cell conversations can be intercepted by creating “fake” cell phone towers that masquerade as legitimate ones.
Finally, some business travelers working in Asia suggest bringing a “burner” PC to places such as China, where the risk of your computer being hacked by malware is especially high. (Don’t connect this PC to your network when returning the office!)
4. Hardware Risks
As we mentioned earlier, many manufacturing facilities rely on a vast range of hardware systems, many of which were designed before cyber-security was much of an issue. Some legacy designs have been upgraded to work over a wireless network, which is convenient, but often, these are not well protected from cyber-intrusions. Commercially available off-the-shelf (COTS) equipment, including Internet of Things (IoT) devices (such as cameras, sensors, etc.) may not have built-in security systems (many use default passwords for example) that make them a risk when adding them to your network. Employees bringing their own devices (BYOD) can also pose a security risk if these devices are not vetted and secured. Take the time to assess each device and determine if it is secure and updated with new patches to the software and firmware.
5. Software Risks
Software and hardware often go hand-in-hand when it comes to security. Unfortunately, many industrial facilities rely on custom legacy apps that were built on software platforms that are out of date. Examples include software running on older Windows operating systems that are no longer supported with frequent security patches (such as Windows98 or Windows 7). Many custom applications are also written using insecure or unsupported programming languages (such as early versions of Java), which makes them inherently insecure. Partnering with a good security consultant will help you identify potential security holes. Update your computers and other devices as soon as new security patches are available. Malware is everywhere and can be embedded in a browser plug-in, mobile phone apps, even legitimate software downloads have been compromised at the server level, such as the recent incident of CC Cleaner, a legitimate program whose source code was infected on the download server. For PC users, investing in paid versions of software virus checkers that constantly scan for rootkits and other nefarious malware intrusions is recommended.
6. Cloud Computing and Web App Risks
Misha Govshteyn, co-founder of the security firm Alert Logic, recently identified web application attacks and cloud misconfigurations as the top two cloud security issues in 2018.
Web applications and cloud-based computing services that connect your network with the outside world can be kept secure — if you implement proactive security configuration management and intrusion detection measures.
Even simple-to-use open source web applications, such as WordPress, can also be compromised, which can damage your reputation and put customer data at risk. Be sure to invest in a cyber-security system solution that monitors and updates your web applications.
7. Network Risks
According to Peckham, one of the key security steps you can take is to segment the topology of your computer network. Why let an intruder or a rogue employee have access to everything? By separating out the network into smaller chunks (connected together with sophisticated routers and NATs), you can put major roadblocks in the way of an intruder.
Pop Quiz: Do you know if your routers are using default passwords? Does your Wi-Fi system have a guest account for visitors without any passwords? These are just two common vulnerabilities that will make it easier for cyber-criminals to access your network. (See item 2 for tips to keep prying eyes away from sensitive network equipment and cables.)
Finally, as secure as your network may be, sneakernet may be the biggest risk of all. For example, an unattended visitor might be able to walk up to an unlocked office PC and start downloading materials directly to a thumb drive. Take steps now to prevent this kind of attack.
8. Financial and Reputational Risks
As we mentioned earlier, the European Union is not playing around. GDPR compliance established a potential fine for compromising or mishandling customer’s private data at $20 million euro or more (up to 4% of the previous fiscal year’s worldwide turnover).
Fines are not the only risk. Direct theft from a company treasury is another. And don’t forget the damage to your company’s reputation that can arise when customers and the public become aware of a significant cyber-attack on your business.
Look into legal agreements and how you can limit your exposure (through indemnification clauses, for example) to errors caused by vendors and partners.
Cyber-attack insurance is another emerging market. Consider evaluating whether this type of coverage would be beneficial to your bottom line.
9. Future Threats
Our final piece of advice is to stay vigilant.
Keep up-to-date on emerging threats as well as those “Zero-Day” attacks that can appear suddenly.
If you have someone, such as a security consultant or staff member, who monitors security events around the world, you’ll be better prepared to act quickly.
For example, learning about a crippling malware event taking place at the start of the business day in Europe could give you a few hours advance notice to ward off a cyber-attack before the workday starts here in America.
Formaspace is Your IT Facilities Partner
If you are looking for ways to make your IT facilities a more comfortable, ergonomic, and pleasant place to work, you’ve come to the right place.
If you can imagine it, we can build it.
From brand new IT departments to sophisticated manufacturing facilities, Formaspace is your go-to expert for IT computer desks, workbench stations, conference tables, and more.
Our technology and manufacturing customers include: Apple, Boeing, Busch, Capital One, Dell, Ford Motor Company, Google, Oculus, Parabola, Toyota, Twitter, and SpaceX.
Why not contact your friendly Formaspace Design Consultant today to learn more about our American-made furniture solutions, built just for you in our Austin, Texas factor headquarters?